Fraud trends explained; how phishing campaigns unfolds
Phishing is a term regularly heard in the news. It’s cybercriminals’ go-to infiltration technique, because it’s simple, and because it works.
Basically, phishing is a type of Internet fraud that seeks to acquire a user’s credentials by deception. It includes theft of passwords, credit card numbers, bank account details and other confidential information.
“Cybercriminals follow trends. They know the latest topics they can effectively piggyback on. It’s a social engineering technique that plays on our human minds, that’s why it’s difficult to resist clicking an unknown link, which may eventually turn out to be malicious,” says Adrian Hia, Managing Director for Asia Pacific at Kaspersky.
For instance, in 2022, key phishing topics monitored by Kaspersky experts related to compensations, bonuses, and even refunds.
Bonuses and compensation are hard to deny in times of crisis and instability, which is why “financial assistance” is frequently promised by con artists to swindle users out of their money.
“Promotional campaigns by major banks” were a popular bait in 2022. Visitors to a fraudulent web page were offered to receive a one-time payment or to take a service quality survey for a fee.
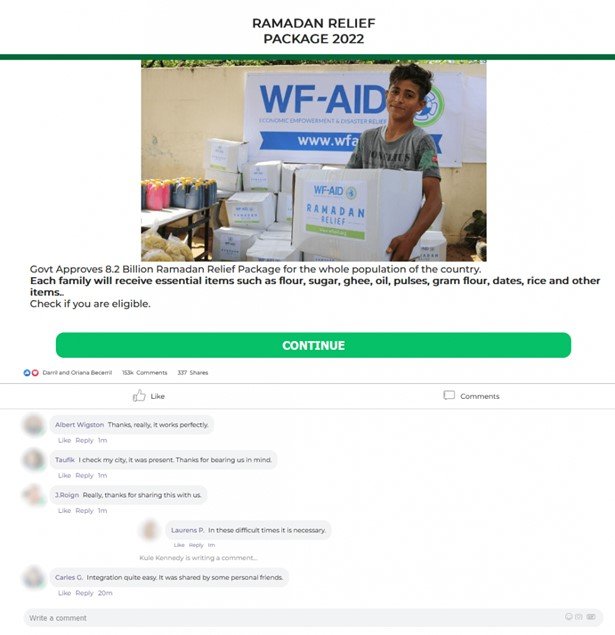
In Muslim countries, scammers promised to send charity packages, purportedly under a “Ramadan Relief” program that aimed at helping low-income families during the Ramadan fast. The fasting period typically sees higher prices for food and household products, whereas observers buy more than they normally do and may be faced with a shortage of money.
Growing utility rates and an increase in the price of natural resources have prompted several governments to start discussing compensations for the population. Payout notices could arrive by mail, email, or as a text message.
Cybercriminals attempted to take advantage of the situation by creating web pages that mimicked government websites, promising cash for covering utility payments or compensation of utility expenses. Visitors were occasionally asked to provide personal details under the pretext of checking that they were eligible, or simply to fill out a questionnaire.
In Singapore, scammers offered a refund of water supply costs, purportedly because of double billing. An energy or resource crisis was not used as a pretext in this particular case, but refunds were still offered in the name of the water supply authority.
“Our solutions blocked more than 43 million phishing attacks against our users in Southeast Asia last year. Clearly, phishing is a tool used frequently by cybercriminals. Because its nature requires a user’s participation – the mere clicking a link or opening of a file – it’s urgent for everyone to know how phishing really works so we can avoid falling prey against it,” adds Hia.
How a phishing campaign unfolds
In 2022, Kaspersky experts saw an increase in spear (or targeted) phishing attacks targeting businesses around the world. In addition to typical campaigns consisting of one stage, there were attacks in several stages. In the first email, scammers in the name of a potential client asked the victim to specify information about its products and services. After the victim responds to this email, the attackers start a phishing attack.
Stage 1: Attackers send an email in the name of a real trade organization requesting more information about the victim company’s products. The email text looks plausible and has no suspicious elements, such as phishing links or attachments. A sender’s email address from a free domain, like gmail.com, may raise doubts. The email on the screenshot below is sent from an address in this domain, and the company name in the From field is different to its name in the signature.
It is worth noting that the use of free domains is not typical for spear phishing in the name of organizations, because such domains are rarely used in business.
Most often in targeted attacks, attackers either use spoofing of the legitimate domain of the organization they are pretending to be, or register domains similar to the original one. In addition, Google and Microsoft are pretty quick in blocking email addresses spotted sending spam. This is the most likely reason why attackers used different addresses in the From header (where the email came from) and Reply-to header (where the reply will go when clicking “Reply” in your email client).
This means the victim responds to another address, which may be located in another free domain, such as outlook.com. The address in the Reply-to header is not used for spam, and correspondence with it is initiated by the victim, so it is less likely to be blocked quickly.
Stage 2: After victims respond to a first email, attackers send a new message, asking them to go to a file-sharing site and view a PDF file with a completed order, which can be found via the link.
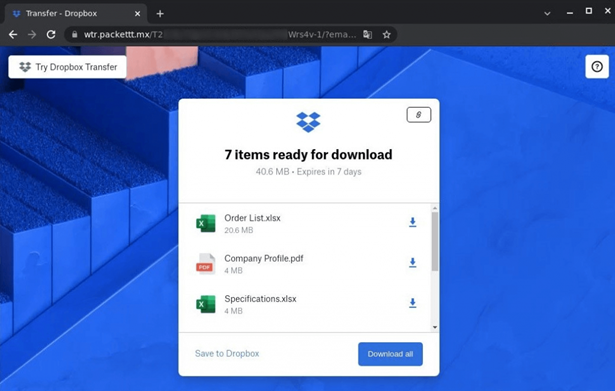
Stage 3: By clicking the link, the user is taken to a fake site generated by a well-known phishing kit. It is a fairly simple tool that generates phishing pages to steal credentials from specific resources. Our solutions blocked fake WeTransfer and Dropbox pages created with this kit.
In the phishing campaign described above, the phishing site mimics a Dropbox page with static file images and a download button. After clicking any element of the interface, the user is taken to a fake Dropbox login page that requests valid corporate credentials.
Stage 4: When victims attempt to log in, their usernames and passwords are sent to https://
The campaign began in April 2022, with malicious activity peaking in May, and ended by June.
Kaspersky identified targets for this campaign around the world, including the following countries: Russia, Bosnia and Herzegovina, Singapore, USA, Germany, Egypt, Thailand, Turkey, Serbia, Netherlands, Jordan, Iran, Kazakhstan, Portugal, and Malaysia.
Phishing trends in 2023
Times of crisis create the preconditions for crime to flourish, including online. Kaspersky experts predict scams promising compensation and payouts from government agencies, large corporations and banks are likely to remain popular among cybercriminals next year.
The unpredictability of the currency market and departure of individual companies from specific countries’ markets will likely affect the number of scams associated with online shopping. At the same time, the COVID-19 topic, popular with cybercriminals in 2020 and 2021, but already beginning to wane in 2022, will finally cease to be relevant and will be replaced by more pressing global issues.
In addition, Kaspersky also has seen an increase in targeted phishing attacks where scammers don’t immediately move on to the phishing attack itself, but only after several introductory emails where there is active correspondence with the victim. This trend is likely to continue. New tricks are also likely to emerge in the corporate sector in 2023, with attacks generating significant profits for attackers.